At a Glance
A critical CVSS 10.0 React vulnerability (CVE-2025-55182) allowed remote code execution in affected React and Next.js apps before patches were available. BlackBox Hosting’s customers remained protected throughout the zero-day window thanks to Fortinet NGFWs and IPS that detected and blocked malicious payloads in real time. Network-level controls stopped exploits before they reached applications, with full logging and visibility for audits and compliance. This shows why proactive security infrastructure is essential when patching alone is too slow.
Severe Vulnerability in React
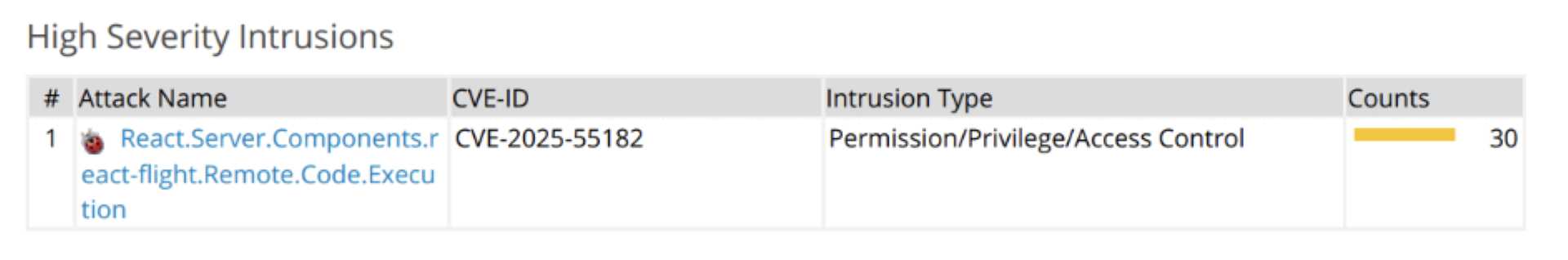
On December 3, 2025, CISA published CVE-2025-55182, a high severity vulnerability. This vulnerability had a severity rating of CVSS 10.0, which is considered the highest in terms of risk.
Millions of React and Next.js-powered services were affected and were at risk from attackers while waiting for patch updates, testing cycles, and deployment windows.
During this time, protection was already in place for customers with BlackBox Hosting. Our strong network security controls safeguard our clients and their applications from day zero, and not just in times of crises.
In this guide, learn more about this vulnerability in React and how our firewalls and IPS stopped it from affecting our customers.
What is CVE-2025-55182?
CVE-2025-55182 is a Remote Code Execution (RCE) vulnerability discovered on November 29, 2025, by Lachlan Davidson. This means an attacker can execute code remotely by deploying a malicious HTTP request to any Server Function endpoint without needing any login credentials or special privileges.
This particular vulnerability in React is grave, as it may affect your apps even if they do not implement any React Server Function endpoints. As disclosed by the React team, this vulnerability exists in versions 19.0, 19.1.0, 19.1.1, and 19.2.0 of 3 React packages:
- react-server-dom-webpack
- react-server-dom-parcel
- react-server-dom-turbopack
It can be present in applications using React Server Components with the App Router if they are running the following versions of Next.js:
- Next.js 15.x
- Next.js 16.x
- Next.js 14.3.0-canary.77 and later canary releases
Given the severity and alarming nature of this vulnerability affecting React and Next.js, it’s critical for users to fix impacted versions immediately.
The Problem with Relying on Updates
A CVSS 10.0 open-source CVE keeps everyone in your network and application security teams on high alert. While the React team has shared recommended updates to mitigate this vulnerability, relying on updates alone is not enough.
Such high severity vulnerabilities leave your business exposed while you coordinate with your technical teams, with each needing to perform some manual fixes to the code for it to work with the updated version. This exposes the cracks in the traditional approach towards open-source security while being both chaotic and disruptive to your organisation.
Instead of relying on updates to fix vulnerabilities, your organisation needs a platform that is built to handle these problems and follows React application security best practices.
How BlackBox Hosting’s Network Security Controls offer Robust Protection
Why wait for updates or stay on unpredictable versions of a package when teams at BlackBox Hosting keep you protected from day zero? Here’s how we protect our customers from Zero-Day CVE-2025-55182 (CVSS 10) and related attacks.
Zero-Day Protection with Fortinet NGFWs and IPS
All our customers using our Fortinet Next Generation Firewalls (NGFWs) with Intrusion Prevention System (IPS) enabled and updated with up-to-date threat intelligence were automatically protected from this exploit, much before patches were made available.
During the active exploitation window, our robust IPS and firewalls were able to:
- Identify malicious patterns associated with CVE-2025-55182
- Block exploit payload attempts in real time
- Prevent any unauthorised and malicious payloads from entering, moving laterally, and executing in customer environments
Our stringent network-based security protocols keep our customers protected when it matters the most and do not solely rely on application patches.
Complete Visibility, Logging and Customer Review
BlackBox Hosting goes beyond blocking attacks and offers complete accountability and verifiable proof that threats were identified and blocked.
With our managed firewall services, our customers gain:
- Full IPS logs and reports of every blocked exploit attempt
- Detailed attack analytics, reviewed regularly
- Full traffic accounting, including the origin and geolocation of the attacks
- Clear audit trails to support ISO 27001, ISO 22301, and other compliance requirements
Optional Network-Based Anti-Virus for Web Applications
BlackBox Hosting offers optional network-based anti-virus scanning at the firewall layer for customers running web applications.
This capability can:
- Scan file uploads before reaching web applications
- Stop and block malware, malicious software, and web shells
- Prevent compromised uploads from entering the application environment
This can add an additional layer of defence to supplement traditional network security controls, which may not be sufficient on their own.
Fortinet’s Purpose-Built ASIC Architecture Powering Uncompromised Performance
All of BlackBox Hosting’s security services are delivered using Fortinet’s purpose-built ASIC hardware, not software-only firewalls. This cutting-edge security architecture keeps performance at scale and consistently delivers ultra-low latency and security inspection at line speed.
Even with IPS, antivirus, traffic analytics and logging enabled, your applications continue to perform reliably and at scale without the hurdles commonly associated with software-based inspection.
Here’s a video that explains more about how we stay ahead in security.
Stay Ahead of CVEs with BlackBox Hosting’s Security Posture
Growing CVEs like CVE-2025-55182 are a clear reminder that businesses can’t solely rely on patching and updates; it may just be too late. Mitigating modern threats requires strong security solutions that go beyond surface-level fixes. To truly stay ahead, your business needs proactive monitoring and in-depth, enterprise-level protection.
BlackBox Hosting’s platform is built with a security-first approach, where you gain:
- Protection from zero-day exploits, as well as ransomware and DDoS attacks
- Enterprise-grade Fortinet NGFWs and deep inspection IPS
- Load balancers with WAF (Web Application Firewall) to protect sites
- Fully managed security options
- Backups managed by Veeam
- Data resilience and recovery with DRaaS; DR replication with 1-second RPO
- Transparent insights and reporting
We offer security, high performance, and reliable cloud and hosting options for all types of businesses. If you run React-based applications and want protection from current and future vulnerabilities in React, contact us today.